Remote work has outpaced legacy security thinking. The traditional network perimeter, once limited to office buildings and managed devices, no longer exists. Work now happens everywhere, across personal devices, cloud platforms, and AI-enabled systems that extend far beyond the enterprise boundary. At Accelare, we help organizations rethink security as a core part of the digital operating model. Through our partnership with Santan Intellect, we integrate Cybersecurity, Privacy, and Risk Management (CPRM) into every stage of transformation, ensuring protection evolves as fast as innovation.
How Remote Work Has Reshaped Security Challenges
Despite record investments of nearly $188 billion globally in information security in 2023, organizations continue to struggle with fragmented defenses and increasing cyber risk. In the same year, 72% of business leaders reported remaining concerned about the security risks associated with remote work. The challenge isn’t a lack of spending or tools. It’s the absence of a coherent, integrated security strategy that evolves in tandem with the business itself.
Traditional VPN-based approaches are a clear example. Once viewed as a secure gateway for remote workers, more than 90% of IT leaders now worry that VPNs actually weaken their overall security posture by creating blind spots in authentication and data visibility. At the same time, the explosion of cloud applications, AI-powered platforms, and bring-your-own-device (BYOD) policies has multiplied the number of access points that must be continuously verified and governed.
What Is Zero Trust Security?
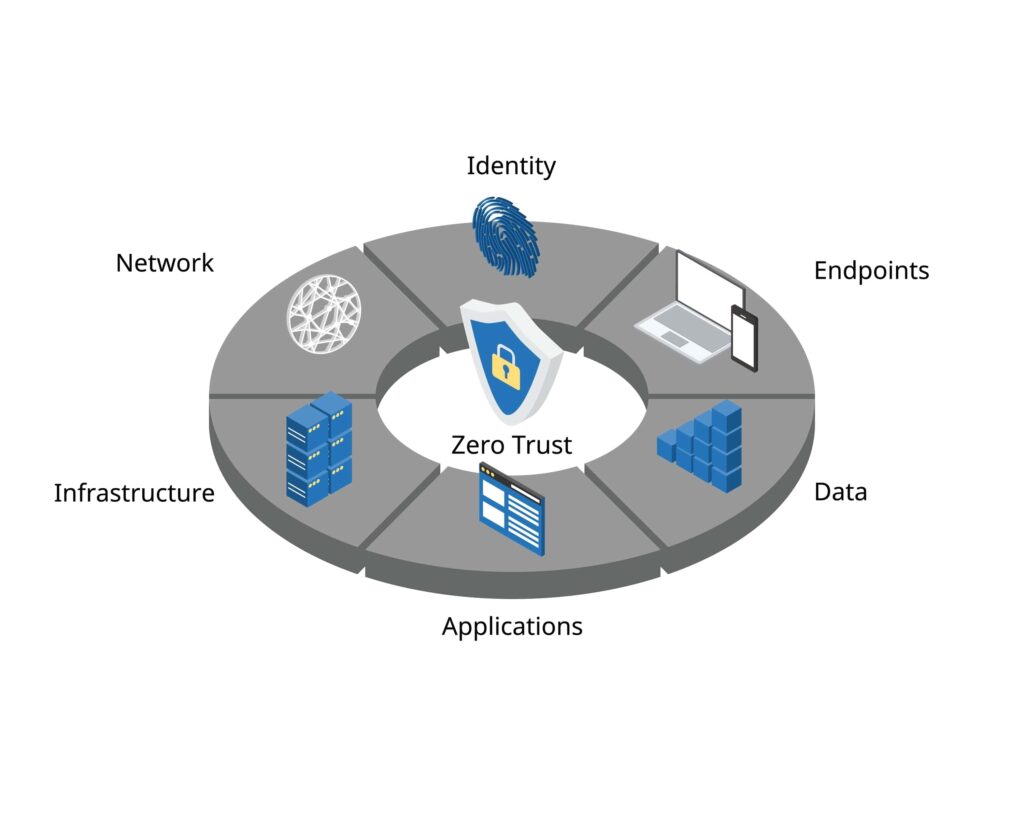
Zero Trust Security is a mindset that assumes every user, device, and connection must be verified continuously. In a remote and cloud-based world, this approach replaces outdated perimeter defenses with dynamic, adaptive protection that follows your people, data, and applications wherever they operate. Zero Trust is built on three core principles:
- Never trust, always verify. Every access request must be authenticated and authorized.
- Assume breach. Design systems that contain threats rather than react to them.
- Least privilege. Give every user only the access required to perform their role.
Key Benefits of Zero Trust for Remote Workforces
Zero Trust establishes the foundation for confident and secure innovation, and provides the following benefits:
- Enhanced Identity and Access Protection: With the Adaptive Identity Security Fabric (AISF), organizations gain continuous verification across users, devices, and platforms, ensuring only the right people have the right access, from anywhere.
- Stronger Application and API Security: The Application Security Protection Fabric (ASPF) safeguards modern and legacy applications through Zero Trust validation and continuous code-level monitoring, thereby reducing supply chain risk.
- Data Privacy and Compliance at Scale: Through the Secure Data Insight Fabric (SDIF), sensitive information is discovered, classified, and protected in real time, which supports compliance and prevents data leaks across cloud and AI environments.
- Resilient Network Infrastructure: The Adaptive Network Security Fabric (ANSF) applies Zero Trust segmentation and AI-driven analytics to secure every connection, whether in the cloud, on-premises, or at the edge.
- Proactive Threat Detection and Response: With the Predictive Threat Response Fabric (PTRF), organizations move from reactive defense to proactive protection. They utilize automation and intelligence to identify and mitigate risks before they disrupt operations.
- Rapid Recovery and Business Continuity: The Incident Response Readiness Fabric (IRRF) ensures business continuity through automated playbooks and coordinated response efforts, minimizing downtime and accelerating recovery.
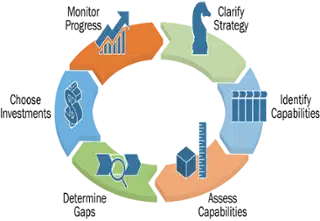
Steps to Implement Zero Trust Security in a Remote Environment
Adopting Zero Trust demands a structured, organization-wide shift in how security is designed, governed, and executed. At Accelare, we guide clients through this transformation using our Strategy-to-Execution framework, so every step strengthens both security and operational performance.
- Define Your Security Purpose and Risk Posture: Every successful transformation starts with clarity. We help leaders align their security strategy with business objectives by identifying critical assets, key risks, and the outcomes Zero Trust must enable.
- Map Capabilities and Access Points: We work with your teams to map where data lives, who accesses it, and how. This step defines the boundaries of Trust and establishes a clear foundation for adaptive identity management and access controls.
- Integrate Platforms and Data Controls: Through the Secure Data Insight Fabric (SDIF) and Adaptive Network Security Fabric (ANSF), we embed visibility and protection across your digital infrastructure, ensuring your Zero Trust framework extends seamlessly to remote and cloud environments.
- Operationalize Governance and Continuous Monitoring: With Santan Intellect’s Predictive Threat Response Fabric (PTRF), we build governance into the daily rhythm of operations. PTRF enables AI-powered detection, automated response, and continuous compliance monitoring.
- Educate, Evolve, and Strengthen Culture: Zero Trust succeeds when people understand their role in maintaining it. Together with Santan Intellect, we deliver executive education and workforce training that builds awareness, accountability, and a lasting security-first mindset.
Strengthen Remote Work Security with Accelare
Remote work has expanded opportunity, but it has also expanded the threat surface. Protecting distributed enterprises requires an operating model where security, privacy, and resilience are built into every connection, workflow, and decision.
At Accelare, we make that possible through our partnership with Santan Intellect.
Contact us today to discuss how our integrated approach to Cybersecurity, Privacy, and Risk Management can help your organization innovate securely and build lasting resilience.
—
References: