As a problem of information asymmetry, digital disruption has flipped the rules of competition. Attackers need only one gap and defenders must protect everything. The unfortunate truth is that legacy trust models tilt the balance against you. Zero Trust is now the gold standard and requires a prescriptive redesign of your security operating model. Done right, it transforms security from a barrier into a platform for safe innovation in the AI era.
Understanding The Importance of Zero Trust Security
Zero Trust is fundamental reworking of the security operating model, the governance fabric that lets you run your current business while you design the next. In an experience-driven, AI-enabled economy, customer value depends on the integrity of the processes that define, build, and deliver that experience. Zero Trust protects those processes, not just the perimeter. Zero Trust also restores balance by verifying explicitly, enforcing least privilege, and assuming breach across identities, apps, data, and networks. The result is less lateral movement, fewer blast-radius surprises, and far more confidence to innovate.
Most organizations approach security with automation thinking, opting for adding tools to speed up what they already do. Accelare’s perspective is different: apply generative, inductive thinking to design a new security model. Ask not, “How do we automate access approvals?” but, “What operating model would eliminate assumed trust and generate safer paths for work to flow?” That shift, from automate to generate, is where Zero Trust becomes transformative rather than incremental.
With this perspective, Zero Trust drives you to be your own best competitor. Waiting for an incident to force change is reactive; using Zero Trust to creatively destroy legacy trust patterns is proactive. You replace brittle perimeter rules with a platform-based security fabric that can evolve every planning cycle. In practice, that means versioning your operating model: securing the As-Is while you build the To-Be.
Common Challenges During Zero Trust Security Implementation
- Legacy Trust Patterns Embedded in the Operating Model: Most organizations still run on architectures built for implicit trust. These patterns are deeply woven into processes and governance, making Zero Trust less about “turning on controls” and more about redesigning how work flows.
- Fragmented Security Tooling: Siloed point solutions create blind spots. Without a unified security fabric, controls are uneven, visibility is partial, and attackers exploit the seams.
- Balancing the As-Is with the To-Be: Executives must secure today’s operating model while building tomorrow’s. Running two versions of the business at once is hard enough. Zero Trust doubles the pressure unless you approach it with versioned governance.
- Cultural Resistance and Change Fatigue: Zero Trust requires substantially more than new technology. It demands a security-first culture that shifts behavior at every level. Without clear narrative and leadership, employees default to old patterns.
- Over-Indexing on Automation Instead of Generation: Organizations often mistake Zero Trust for a set of automated access controls. The challenge is moving beyond automation to generative design. Rethink the operating model so unsafe paths never exist in the first place.
- Information Asymmetry with Adversaries: Attackers exploit one overlooked exception or unpatched rule. Defenders face the harder task of being right everywhere, all the time. Zero Trust mitigates this imbalance, but only if implementation is systemic and consistent.
Key Steps to Implementing Zero Trust Security
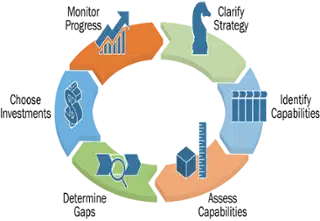
- Define the Security Operating Model: Start by mapping your governance fabric: who owns processes, how decisions flow, and where trust is currently assumed. This creates the blueprint for versioning Zero Trust into your As-Is and To-Be models. This task also sets the foundation for orchestrating layered Security Fabrics as one unified operating model.
- Establish Identity as the New Perimeter: Adopt adaptive identity security. Every user, device, workload, and service must be explicitly verified and continuously authenticated. No more implicit passes. Adaptive Identity Security Fabric (AISF) provides identity governance, risk-based authentication, adaptive access controls, and continuous verification.
- Apply Least-Privilege Access Everywhere: Shift from role-based broad access to granular, just-in-time permissions. Design processes so work can flow only through verified, minimal-exposure pathways. AISF enforces least privilege dynamically, ensuring the right individuals have the right access at the right time.
- Secure Data at the Core: Discover, classify, and protect sensitive information wherever it resides, including in applications, cloud, edge, or AI pipelines. Data integrity becomes the anchor of trust. Secure Data Insight Fabric (SDIF) automates discovery, classification, and policy-based controls, preventing breaches and data poisoning.
- Segment and Strengthen the Network Fabric: Use Zero Trust segmentation to contain lateral movement. Treat every connection as untrusted until validated, and dynamically adapt based on behavior and context. Adaptive Network Security Fabric (ANSF) employs AI-driven analytics and Zero Trust segmentation across cloud, on-prem, and edge.
- Integrate Continuous Threat Detection and Response: Replace fragmented monitoring with predictive and automated defenses. Zero Trust requires resilience: fast detection, orchestrated response, and minimal blast radius. Predictive Threat Response Fabric (PTRF) unifies detection, automated response, and resilience into a single platform.
- Build a Culture of Security-First Behavior: While technology is a key component, alone it cannot deliver Zero Trust. Embed awareness, education, and accountability into the operating model so secure behavior becomes the default, not the exception. Accelare and Santan Intellect deliver tailored education and awareness programs aligned to transformation goals.
- Version Your Zero Trust Implementation Plan: Design the transformation as an iterative process: secure the As-Is, architect the To-Be, and continuously evolve the model every planning cycle. Incident Response Readiness Fabric (IRRF) ensures the business can pivot quickly, securing today’s operating model while designing the next.
Develop a Zero Trust Implementation Plan with Accelare
Security shouldn’t slow transformation; it should accelerate it. A Zero Trust operating model, supported by Accelare’s Security Fabrics, empowers organizations to innovate in the age of AI without compromising resilience or compliance.
Talk to Accelare today and discover how Zero Trust can power your transformation.
—